What Event Caused the Transformation From the Art of Cryptography to the Science of Cryptography?
What is cryptography?
Cryptography is a method of protecting information and communications through the employ of codes, so that just those for whom the data is intended can read and process it.
In information science, cryptography refers to secure information and communication techniques derived from mathematical concepts and a ready of rule-based calculations called algorithms, to transform messages in ways that are hard to decipher. These deterministic algorithms are used for cryptographic key generation, digital signing, verification to protect data privacy, web browsing on the internet and confidential communications such equally credit card transactions and email.
Cryptography techniques
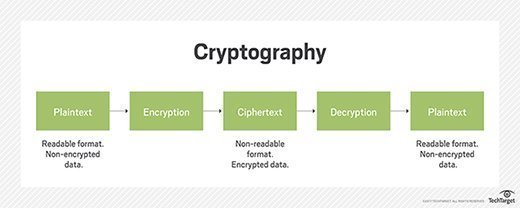
Cryptography is closely related to the disciplines of cryptology and cryptanalysis. It includes techniques such as microdots, merging words with images and other ways to hibernate data in storage or transit. However, in today's computer-centric world, cryptography is about often associated with scrambling plaintext (ordinary text, sometimes referred to as cleartext) into ciphertext (a process called encryption), so dorsum again (known as decryption). Individuals who practice this field are known as cryptographers.
Mod cryptography concerns itself with the following four objectives:
- Confidentiality. The information cannot be understood by anyone for whom information technology was unintended.
- Integrity.The information cannot be altered in storage or transit between sender and intended receiver without the alteration existence detected.
- Non-repudiation. The creator/sender of the data cannot deny at a afterwards stage their intentions in the cosmos or manual of the information.
- Authentication. The sender and receiver tin can confirm each other's identity and the origin/destination of the data.
Procedures and protocols that meet some or all of the in a higher place criteria are known equally cryptosystems. Cryptosystems are often thought to refer only to mathematical procedures and computer programs; however, they also include the regulation of human behavior, such as choosing hard-to-guess passwords, logging off unused systems and not discussing sensitive procedures with outsiders.
Cryptographic algorithms
Cryptosystems use a gear up of procedures known as cryptographic algorithms, or ciphers, to encrypt and decrypt messages to secure communications among computer systems, devices and applications.
A cipher suite uses 1 algorithm for encryption, another algorithm for message authentication and another for key exchange. This process, embedded in protocols and written in software that runs on operating systems (OSes) and networked figurer systems, involves:
- public and individual key generation for data encryption/decryption
- digital signing and verification for bulletin hallmark
- key exchange
Types of cryptography
Unmarried-key or symmetric-cardinal encryption algorithms create a stock-still length of bits known as a block nada with a surreptitious key that the creator/sender uses to encipher data (encryption) and the receiver uses to decipher information technology. Ane example of symmetric-key cryptography is the Advanced Encryption Standard (AES). AES is a specification established in November 2001 by the National Institute of Standards and Applied science (NIST) as a Federal Data Processing Standard (FIPS 197) to protect sensitive data. The standard is mandated by the U.Southward. regime and widely used in the individual sector.
In June 2003, AES was canonical by the U.S. government for classified information. It is a royalty-complimentary specification implemented in software and hardware worldwide. AES is the successor to the Data Encryption Standard (DES) and DES3. It uses longer key lengths -- 128-bit, 192-scrap, 256-bit -- to prevent brute force and other attacks.

Public-key or asymmetric-key encryption algorithms apply a pair of keys, a public primal associated with the creator/sender for encrypting messages and a private central that only the originator knows (unless it is exposed or they decide to share it) for decrypting that information.
Examples of public-central cryptography include:
- RSA, used widely on the net
- Elliptic Bend Digital Signature Algorithm (ECDSA) used past Bitcoin
- Digital Signature Algorithm (DSA) adopted every bit a Federal Information Processing Standard for digital signatures past NIST in FIPS 186-four
- Diffie-Hellman key exchange
To maintain information integrity in cryptography, hash functions, which return a deterministic output from an input value, are used to map data to a fixed data size. Types of cryptographic hash functions include SHA-1 (Secure Hash Algorithm ane), SHA-2 and SHA-iii.
Cryptography concerns
Attackers can featherbed cryptography, hack into computers that are responsible for data encryption and decryption, and exploit weak implementations, such as the employ of default keys. However, cryptography makes it harder for attackers to access messages and data protected by encryption algorithms.
Growing concerns about the processing power of breakthrough calculating to break current cryptography encryption standards led NIST to put out a call for papers amongst the mathematical and science community in 2016 for new public primal cryptography standards.
Unlike today's computer systems, quantum computing uses breakthrough bits (qubits) that tin represent both 0s and 1s, and therefore perform two calculations at once. While a large-scale quantum computer may non be built in the next decade, the existing infrastructure requires standardization of publicly known and understood algorithms that offer a secure approach, according to NIST. The deadline for submissions was in Nov 2017, assay of the proposals is expected to accept three to five years.
History of cryptography
The word "cryptography" is derived from the Greek kryptos, meaning hidden.
The prefix "crypt-" ways "hidden" or "vault," and the suffix "-graphy" stands for "writing."
The origin of cryptography is unremarkably dated from near 2000 B.C., with the Egyptian exercise of hieroglyphics. These consisted of complex pictograms, the full significant of which was only known to an elite few.
The kickoff known apply of a modern null was by Julius Caesar (100 B.C. to 44 B.C.), who did not trust his messengers when communicating with his governors and officers. For this reason, he created a organisation in which each character in his messages was replaced by a character three positions ahead of it in the Roman alphabet.
In contempo times, cryptography has turned into a battleground of some of the world'southward best mathematicians and computer scientists. The power to deeply store and transfer sensitive information has proved a critical factor in success in war and business.
Because governments do not desire certain entities in and out of their countries to have access to ways to receive and send hidden information that may be a threat to national interests, cryptography has been subject to various restrictions in many countries, ranging from limitations of the usage and export of software to the public dissemination of mathematical concepts that could be used to develop cryptosystems.
Still, the internet has allowed the spread of powerful programs and, more chiefly, the underlying techniques of cryptography, so that today many of the most advanced cryptosystems and ideas are now in the public domain.
This was final updated in September 2021
Go along Reading About cryptography
- Cryptography quiz questions and answers: Test your smarts
- Quantum computers mean cryptography needs to alter, and soon
- What is mail-breakthrough cryptography and should nosotros intendance?
- Weighing double key encryption challenges, payoffs
- Find out what's new in cryptography from NIST
Dig Deeper on Identity and access management
-

quantum cryptography
-

cryptographic checksum
-

RSA algorithm (Rivest-Shamir-Adleman)
-

cipher
hansonverlable1941.blogspot.com
Source: https://www.techtarget.com/searchsecurity/definition/cryptography




0 Response to "What Event Caused the Transformation From the Art of Cryptography to the Science of Cryptography?"
Post a Comment